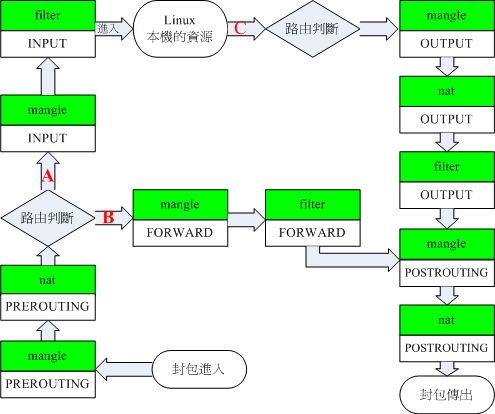
架构图
开启转发
# 存在第一条net.ipv4.ip_forward=0,ansible会删除net.ipv4.ip_forward = 1
sed -i 's/^net.ipv4.ip_forward.*/net.ipv4.ip_forward = 1/g' /etc/sysctl.conf
# 没有生效则追加
sysctl -p|grep -q 'net.ipv4.ip_forward = 1' || echo 'net.ipv4.ip_forward = 1' >> /etc/sysctl.conf && sysctl -p
最小示例
# Generated by iptables-save v1.4.7 on Mon Oct 12 16:57:10 xxxx
# 所有的数据流都会通过nat链路,所以POSTROUTING默认DROP时会导致网关无法telnet其它服务器
*nat
:PREROUTING ACCEPT [537:62529]
:POSTROUTING ACCEPT [2:160]
:OUTPUT ACCEPT [2:160]
# 访问本机1136端口,则nat到192.168.1.100的3306端口
-A PREROUTING -i eth0 -p tcp --dport 1136 -j DNAT --to-destination 192.168.1.100:3306
# 流向192.168.1.100的3306端口的数据,将源ip改为本机ip
-A POSTROUTING -d 192.168.1.100 -o eth0 -p tcp -j SNAT --to-source 192.168.1.99
COMMIT
*filter
# 注意FORWARD一定要开启ESTABLISHED,否则会出现回包失败
:FORWARD DROP [0:0]
-A FORWARD -p tcp -m state --state RELATED,ESTABLISHED -j ACCEPT
# 允许访问nat数据的ip为:company_ip,类似filter链的INPUT规则
-A FORWARD -p tcp -s company_ip -d 192.168.1.100 --dport 3306 -j ACCEPT
COMMIT
